Cleaning up an infected PHP server (Mal/Badsrc-M – Troj/PHPShll-B)
29 Oct 2012I recently discovered that a number of sites of mine were considered unsafe by Google, Firefox, Yandex … The reason was they had detected malware being served to visitors of the site. I checked a bit further and I discovered it was the Mal/Badsrc-M – Troj/PHPShll-B trojan. In each of my (WordPress and other) PHP files, the first line had been changed to:
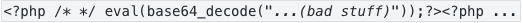
The file is easy to clean up: you remove the eval statement and that’s it. Only, on this server several hundreds of PHP files (WordPress, MediaWiki, …) were affected. So I made a script to go through all of them and clean up. It uses the fact that
- the whole injected statement is on the 1st line
- no ‘decent’, trustworthy program uses the base64 trick in its PHP code
it moves the second<?phpto the second line and then removes the whole first line- it does everything in 1 awk statement
So if you have the same problem, use a bash script like this and run it in the root of all your websites: